
Azure Functions can expose API endpoints (HttpTriggers). By default those Http endpoints are only protected by a function key that needs to be sent along. As this is not very secure, most companies that use Azure Functions with API endpoints want to secure them through Entra ID. This is in fact really easy and configurable without writing a single line of code. But the default setup is not entirely optimal. This blog post highlights one subject to look at to make it better.
Scenario
Say we want to build an API that can be called from the SharePoint Framework (for example). An Azure Function would be a great option there, as it’s easy to build an API with it. We would need a Function with HttpTriggers and some Entra ID authentication enabled above the usual function key setup.
Configuring Entra ID authentication on an Azure Function can be done using code, for example adapting the .NET pipeline with some authentication middleware. It’s not very hard and it’s super flexible, but there’s some steps to take, tests to do and some code to review. Instead of coding, you can also simply enable the built-in authentication. It’s a feature of the App Service infrastructure, and it can be configured with either Azure Functions or App Services. It’s as easy as flipping the switch and you can even select multiple identity providers.
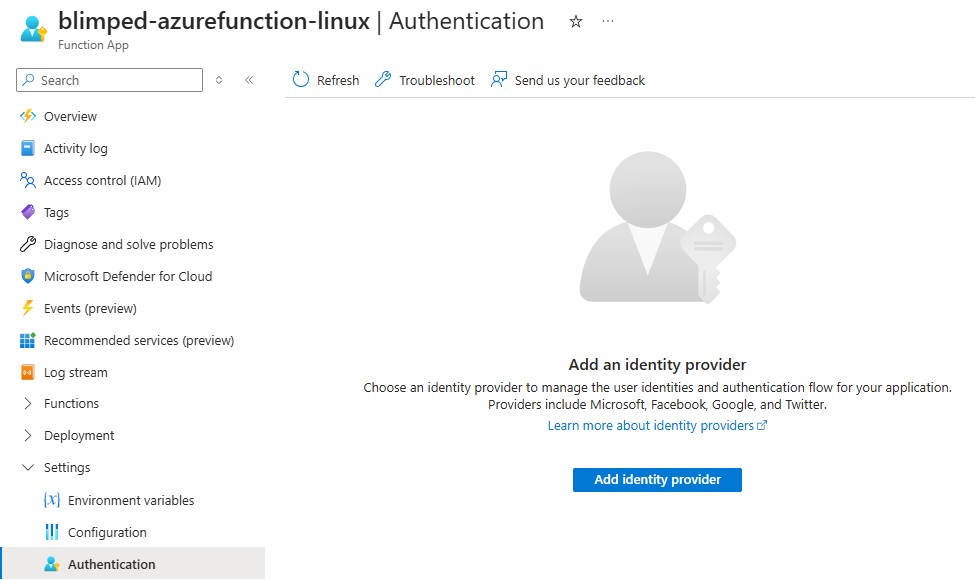
Allowing Azure to provision an App Registration
When building extensions for Microsoft 365, I’m mostly just interested in the Entra ID Identity Provider. When enabling this provider it will allow you the option to select an App Registration for authenticating your Azure Function. Instead of creating my own app registration manually, I mostly select the option to let Azure provision it for me. It’s easier because it will set it up precisely as needed.
…or so I thought. So I initially overlooked the reason for Azure to want to create a Client Secret on the application:
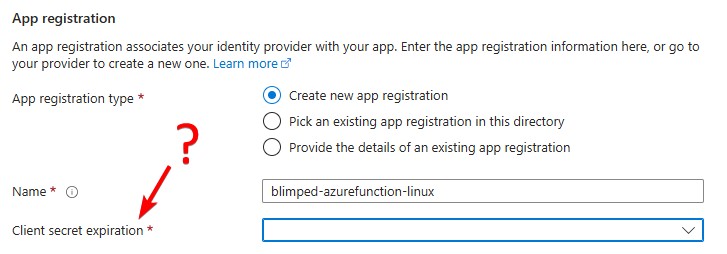
The mentioned Client Secret is created on the Entra app registration and added to the Azure Function environment variables section:
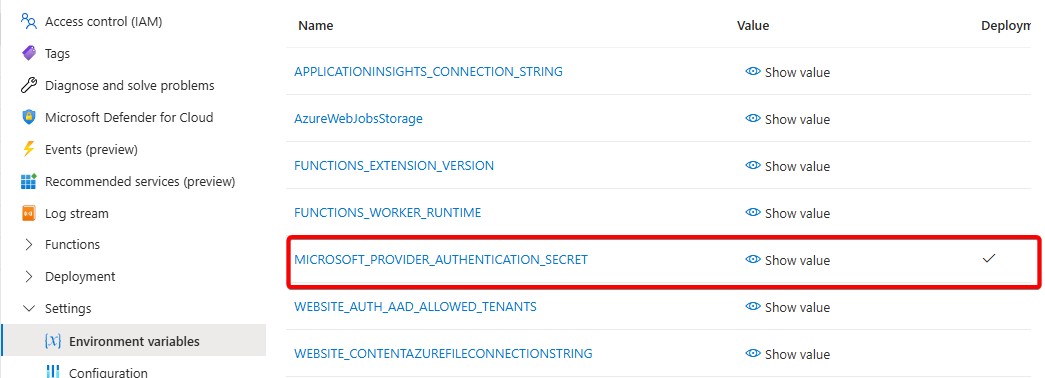
But this setup is actually annoying for a couple of reasons:
Administrative burden
You’ll need to factor in that the Client Secret will eventually expire. Recreating the secret will need to be added to someones IT Admin calendar. In short: secrets add an administrative burden.Insecure practice
Adding a secret to the environment variables like this is not exactly a safe practice, anyone with read-only access to the resource would be able to read it. To make it secure you would need to add a KeyVault to the solution, making the application architecture more complex and expensive.
Looking at the provisioned app registration
When looking at the provisioned application, we can see that the Client Secret is indeed configured:
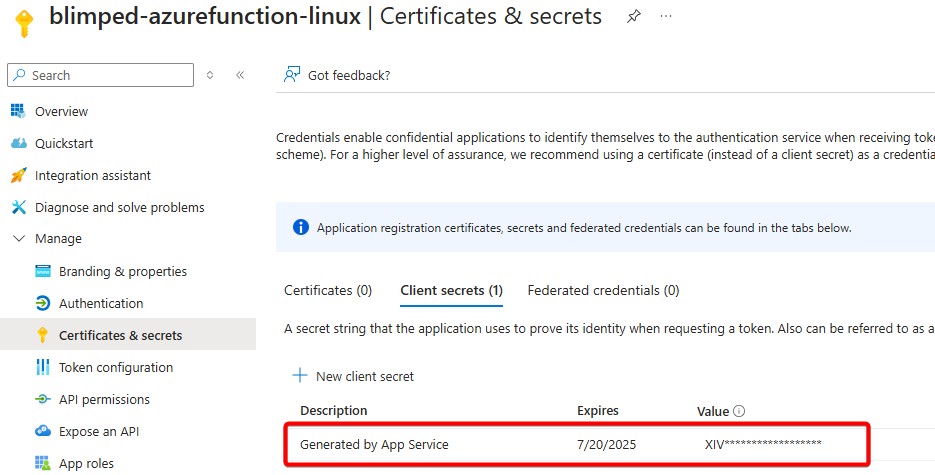
But there’s something else as well, in the authentication section, it appears that the Web platform has been added with a specific redirect URL and ID tokens enabled:
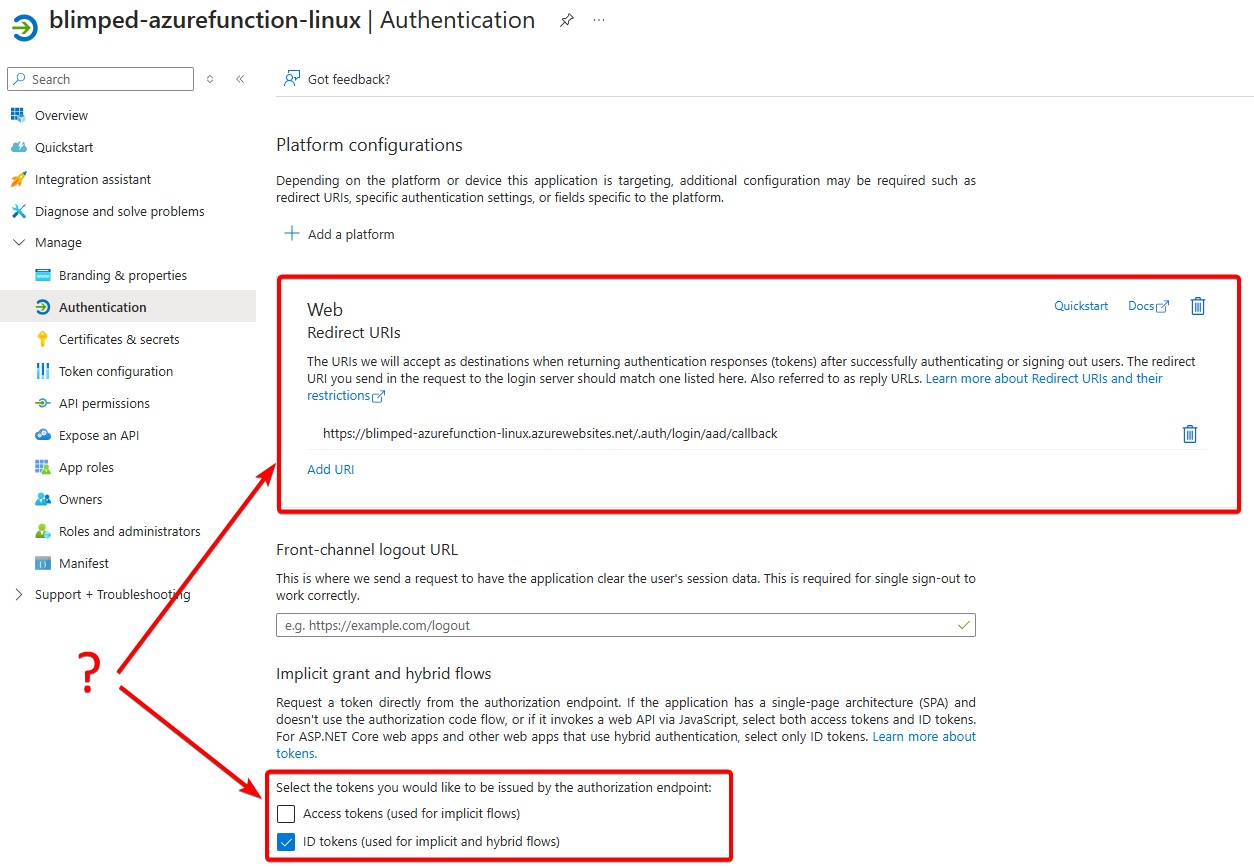
…and therein lies the crux of the matter. That configuration would be logical for a Web Application that would challenge and redirect users to login.microsoftonline.com if they would visit the site and click a login button. The built-in authentication would use the Authorization Code flow to authenticate the user. And that’s the reason for the added client secret as well. The Azure Function will use the Client Secret in the Authorization code flow to request an access token while redeeming an authorization code.
So in a sense this provisioned app registration / authentication setup can be used for securing both a Web Application and an API!
Getting to an optimal setup
You could use an Azure Function to serve HTML, so as to work (kind of) as a website. But most people (me included), will probably just use it for API-stuff (or for webjob-stuff). So my Azure Function won’t redirect users to login.microsoftonline, it won’t allow them to be redirected back to the expected redirect URL. In fact, my Azure Function will not even request an Access Token. The calling application (In this scenario that’s SharePoint Framework) will request an Access Token for this Azure Function app and will send it along to the HttpTrigger. If no access token is sent, or it is incorrect or expired, the Azure Function will simply respond with a 403 Forbidden or 401 Unauthenticated HTTP response.
So we can effectively just clean this up to a more minimal setup that works for an API and not for a Web application!
Cleaning up the setup
So what you can do is the following:
- Remove the Web platform from the Authentication section of the App Registration.
- Remove the Client Secret from the Certificates & Secrets section of the App Registration.
- On the Azure Function configuration remove the
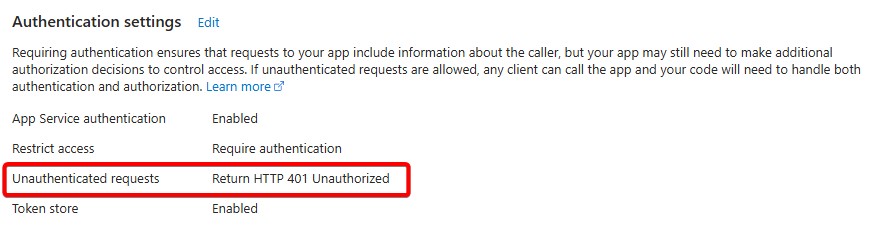
MICROSOFT_PROVIDER_AUTHENTICATION_SECRETenvironment variable / app setting. - Make sure you’ve configured the authentication settings of the Azure Function to return a 401 response on unauthenticated requests:
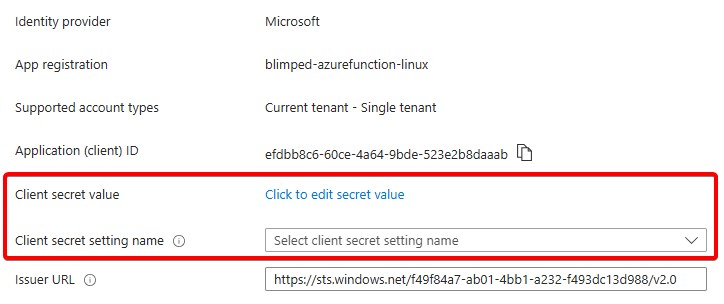
If you now edit the identity provider settings, you’ll notice that the fields for the Client Secret are empty. And that’s OK!
And you’re done! The Authentication will keep working as expected, and you’ll make your IT Admin a bit happier!
Conclusion
Enabling built-in authentication on an Azure Function is a very simple and powerful feature. However, by default it will provision an app registration that can be used for both Web Applications as well as API’s. Cleaning that up to a more minimal setup is wise, to lessen the administrative burden and the impact of additional resources and costs.
🚀 I hope you enjoyed this post or learned something new! Happy coding! 🚀
Sources
- Microsoft Docs - Authentication and authorization in Azure App Service and Azure Functions
- Microsoft Docs - Microsoft identity platform and OAuth 2.0 authorization code flow - Request an access token with a client_secret
auth azurefunction entraid
More
More blogs

Release Branch Strategies in CI/CD with Federated Identity - GitHub edition
Learn how to secure SPFx deployments using GitHub Actions and Federated Identity with release branch strategies. A deep dive into flexible federated credentials for effective CI/CD security.
Read more
Deploying to Microsoft 365 using the CLI and federated identity - DevOps edition
Learn how to properly deploy artifacts from Azure DevOps Pipelines to Microsoft 365 using the CLI for Microsoft 365 without fiddling with certificates or user credentials.
Read more
Deploying to Microsoft 365 using the CLI and federated identity - GitHub edition
Learn how to properly deploy artifacts from GitHub workflows to Microsoft 365 using the CLI for Microsoft 365 without fiddling with certificates or user credentials.
Read moreThanks
Thanks for reading

Thanks for reading my blog, I hope you got what you came for. Blogs of others have been super important during my work. This site is me returning the favor. If you read anything you do not understand because I failed to clarify it enough, please drop me a post using my socials.
Warm regards,
Martin
Microsoft MVP | Microsoft 365 Architect