

Guest access in SharePoint is a great feature. Allowing people from other organisations to read or even collaborate on documents is an increasing phenomenon as more organisations are embracing Microsoft 365. And yet, it suffers from a few minor flaws in my view. Up till now.
SharePoint works in mysterious ways…
The issues occur when you allow your users to invite new guests from SharePoint and OneDrive:
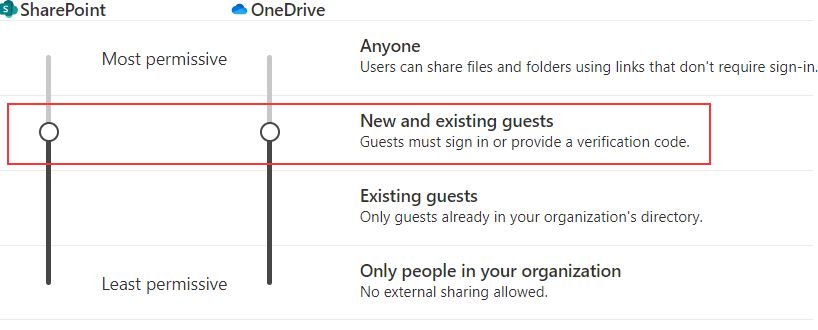
As long as you’re inviting people into your Entra ID first, and let them go through the invite redemption process, accessing SharePoint afterwards works like a glove. The key word here is ‘afterwards’. Guest access with existing guests works fine. The issues I’m talking about start as soon as you want to invite NEW guests and you’re starting in SharePoint. This is a quite normal scenario, as an average user would not think to approach IT, he’ll just hit the ‘Share’-button and try it out.
…when sharing a file or folder with a new guest
When the average user in question would share a file or folder with a new guest, that new guest will be able to get to the document. That part works fine. But he’ll be a special type of user, a SharePoint-only email auth guest or Ad hoc external recipient. The problem is: this kind of user will not end up in Entra ID. Even though he might (over time) be granted access to a lot of documents and folders. It’s like Mr X in the ‘Scotland Yard’ board game. You never know where he is, unless you happen to step on him. He’s not even really signing in, he’ll be able to open the document using a verification code, which looks a lot like the new Entra ID one-time passcode (OTP) functionality, although it’s not the same: even if you’ve disabled OTP, guests will still be able to use this verification code to sign in.
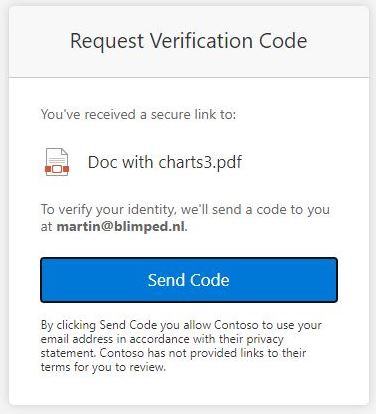
Not being able to find these users in Entra ID not ideal in my opinion. What if you want to monitor sign-in activity for these guests, or what if you would want to block the user from accessing tenant resources? Or apply Entra Conditional Access policies? There is no clarity and no control.
…when sharing an entire SharePoint site with a new guest
When the average user in question would share an entire site with a new guest, we see different behavior. In this case, the user will eventually be added to Entra ID, which is good. But he’ll not get the default Entra ID invitation redemption experience. He’ll get the old-fashioned SharePoint version. He’ll be asked to sign in using a Microsoft Account or Organisational account. Other federation options are not supported, even if configured in Entra ID. And OTP is also not supported here. On top of that: if you’re already signed in with your organisational account, and you click on the sharing-link, you might even not be able to redeem your invite. You might get stuck on this error:
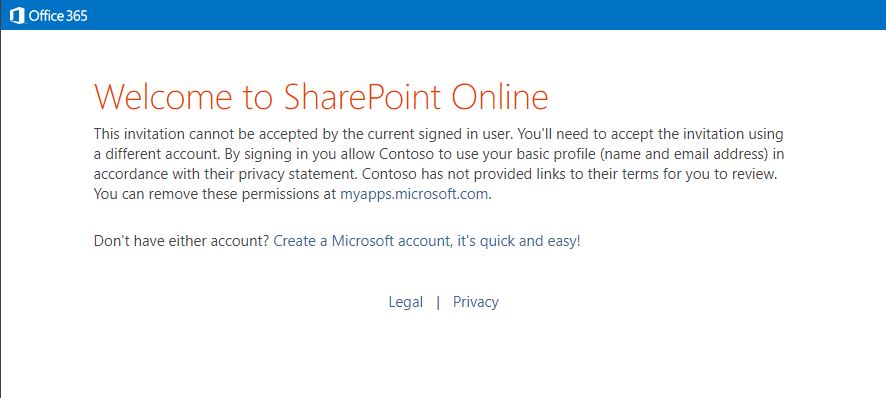
… so is that problematic?
Is all that problematic? You could of course just disable new guests in SharePoint, but you loose a lot of powerful functionality when you do that. These little flaws mainly show what’s going on here: that there are still some areas where SharePoint and Entra ID aren’t really integrated very well. And more of these kind of little inconsistencies surface if you’re working with the tools longer.
Solution
Luckily Microsoft has been changing things. A new feature has been rolling out which makes it possible to enable a better integration between SharePoint and Entra ID which solves the issues mentioned above: new guests will always be added to Entra ID, and they’ll always go through the default Entra ID invite redemption experience plus a few extra bonuses on top of that. SharePoint and Entra ID will now work together in a more logical way. And all that by configuring it with two lines of SharePoint Online PowerShell. Be sure to install the latest version of the commandlets and run the following:
Connect-SPOService -Url "https://<tenant>-admin.sharepoint.com"
Set-SPOTenant -EnableAzureADB2BIntegration $true
Set-SPOTenant -SyncAadB2BManagementPolicy $true
Or use the CLI for Microsoft 365, version >= 5.2.0:
m365 spo tenant settings set --EnableAzureADB2BIntegration true
m365 spo tenant settings set --SyncAadB2BManagementPolicy true
SharePoint guest access and OTP
There is one important thing to keep in mind here: this change is riding on the back of another important new feature, Email one-time passcode authentication (OTP). OTP is the recent Entra External Identities feature that Microsoft is pushing where you can redeem an invite and sign into another Entra ID by filling in a verification code that was sent to your emailaddress. It’s a great feature which will among other things put an end to viral tenants. Guest users will only be using the feature if they do not have a personal or organisational Microsoft account. Or a Google account for that matter, if Google federation was configured on your tenant. See this helpful redemption flow diagram to understand when it will be used.
So OTP is an optional setting that allows for a quicker invite redemption and sign in experience for some guest users. Microsoft initially communicated that this setting would be enabled by default in October 2021, but the deployment schedule has been changed, the setting will now be enabled by default in July 2022. You can opt out or opt in though.
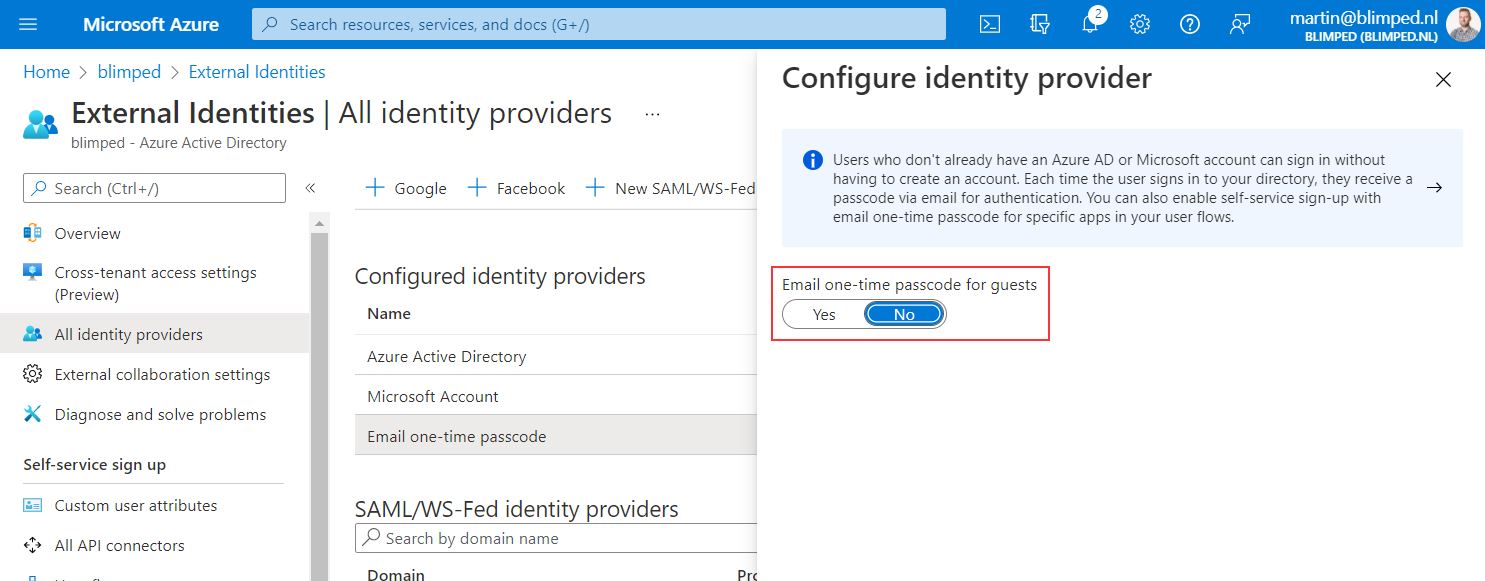
And that’s important, because if you opt out, you’ll not be able to use the new SharePoint and Entra B2B integrated experience. If you haven’t enabled OTP and you execute the commandlets, you’ll get the following warning:
WARNING: Make sure to also enable the Entra one-time passcode authentication preview. If it is not enabled then
SharePoint will not use Entra B2B even if EnableAzureADB2BIntegration is set to true. Learn more at
http://aka.ms/spo-b2b-integration.
If you do not enable OTP after this, the integration feature will just not work. SharePoint guest access will just keep working like it did before. There’s probably some technical reason why Microsoft has made this integration so dependant on OTP. But for those who don’t want to use OTP for some reason or other I hope that this will change in the future. Let’s see where time brings us.
Parting words
Microsoft is doing some great work here in modernizing the SharePoint guest access experience. End users as well as IT Administrators will benefit from these things greatly. The only drawback is the reliance on OTP. I hope that even tenants without OTP enabled will in the future benefit from the integration. However it is, it’s good work in the right direction.
Any thoughts, feedback or additions are welcome.
Sources
- SharePoint Azure B2B Integration
- B2B Collaboration overview
- Email one-time passcode authentication (OTP)
- Adding the integration options to the CLI Microsoft 365
- OTP and the redemption flow
- About SharePoint Guest Access
sharepoint guest access entraid
More
More blogs

Running applications with limited SharePoint permissions
Securing application access to SharePoint through Entra ID is easy, but how to access SharePoint using the principle of least privilege?
Read more
Getting notified of changes in guests accessing SharePoint
Part 3 on how to use the CLI for Microsoft 365 and Azure Functions: How to get notified of updates in guests accessing SharePoint.
Read more
Resource Specific Consent - Using delegated Sites.Selected
Sites.Selected has been made available in delegated mode! What does it mean and how does it work?
Read moreThanks
Thanks for reading

Thanks for reading my blog, I hope you got what you came for. Blogs of others have been super important during my work. This site is me returning the favor. If you read anything you do not understand because I failed to clarify it enough, please drop me a post using my socials.
Warm regards,
Martin
Microsoft MVP | Microsoft 365 Architect